TEN Explained: Immersion in a Unique L2 and Ecosystem
An inside look at how TEN, which is neither Optimistic nor zk-rollups, works and how the ecosystem around it is built.
Disclaimer: The content presented in this article, along with others, is based on opinions developed by the analysts at Dewhales and does not constitute sponsored content. At Dewhales, we firmly adhere to a transparency-first philosophy, making our wallets openly available to the public through our website or DeBank, and our articles serve as vehicles for self-expression, education, and contribution to the ecosystem.
Dewhales Capital does not provide investment advisory services to the public. Any information should not be taken as investment, accounting, tax or legal advice or as a recommendation to purchase, sell or hold or to pursue any investment style or strategy. The accuracy and appropriateness of the information is not guaranteed by Dewhales Capital.
Introduction
1. TEN Network overview
2. TEN Network architecture
3. POBI Consensus Mechanism
4. Partnerships, ecosystem and direct usecases
5. Tokenomics
6. Team
7. Backers
Conclusion
Introduction
Note: since the project was previously called Obscuro and the old name is used in some materials, sometimes Obscuro may be mentioned instead of TEN.
TEN's main feature, compared to other L2 solutions, which have become quite numerous lately, is that it is encrypted and offers the ability to use confidential smart contracts on Ethereum. Thus, TEN allows Ethereum smart contracts to contain both public and private states. Moreover, full compatibility with Ethereum dApps is promised, and users and developers will not have to change their approach to development and user experience. Let's consider what exactly this means and how it works.
1. TEN Network overview
TEN supports two different processes: transaction encryption and confidential computations, opening up an entirely new realm of use cases. Transactions are encrypted with various keys that can be independently disclosed. This feature is inherited from the previous Corda development, which was oriented towards the banking sector and offered the ability to track transactions without client access. However, TEN's use cases extend far beyond concealing confidential financial information. These examples will better illustrate the logic behind TEN and encryption, despite the protocol's complexity (in a separate section, we will further explore the practical implementations of these use cases):
Gaming: Although TEN appears to be a project with a strictly financial and technical focus, its technology can be used, for instance, to create a fog of war in games, where one player cannot see another player's territory. Another example, TEN's logic can enable a scenario where in a poker game, all cards on the table are visible, but cards in a player's hands are visible only to them.
Smart contracts can have two states: public and private.
Private agreements: Participants can only see necessary information.
KYC: Participants who have passed KYC can only disclose partial information, and TEN offers a native solution for this implementation without the need for separate mechanisms.
Sealed auctions/sales rounds: Buyers and sellers make closed bids that can later be disclosed publicly or privately.
Moreover, TEN natively uses the entire EVM and so supports executing Ethereum bytecode without using compilers and native languages as in zkSync, Starknet, and other rollups. However, there are differences in data structure because:
The rollup structure itself differs from the Ethereum block structure.
The data structure contains additional information about encrypted transactions, instructions for outputting plaintext, events, links to L1 blocks, and more.
TEN's RPC API is similar to a typical Ethereum node, but all request/response data is encrypted, and some methods are inaccessible. For example, a developer cannot call getStorageAt() to directly leak the contract state. That is, the main difference between TEN's RPC API is that it expects everything to be delivered as encrypted blocks.
On the user-observer side, this means that the same amount of data cannot be retrieved as in Etherscan and its based explorers on EVM networks. The user will be able to see the transactions on their wallet that relate to their account, but otherwise they are limited to publicly available higher level information such as batch and summary hashes. That is, one can see the number of transactions, but no details.
Also, TEN cannot be precisely classified as zk-rollups because it does not use zk-proofs, or as optimistic rollups because it has significant differences from them and has a 1-day delay period instead of 1 week for optimistic rollups. Moreover, this period can be reduced to 10 minutes as the number of TEN nodes increases.
Another fundamental difference is that TEN uses the principle of L1 and L2 synchronization based on timestamps to synchronize balance changes in L1 and L2 (this is somewhat similar to the timestamp synchronization principle in BTC on the Babylon Chain). This also minimizes fork risks, which are minimal thanks to TEEs. Additionally, transactions are processed sequentially, and L2 nodes processing them stake TEN tokens for guarantees of fair behavior. Depending on their behavior, they receive rewards, or slashing may occur.
In addition to all the aforementioned features, TEN offers another fundamental change compared to traditional zk-rollups. Namely, the ability to configure the decryption period, which can be crucial for financial applications. That is, initially, transactions are decrypted and executed within TEN and stored in encrypted form. Then, after a certain period of time, the information in them may become publicly accessible like in any public blockchain. Moreover, each time interval during which the information remains encrypted is encrypted with шиdifferent keys. That is, a data structure containing the initial (index) position of each parameter is created separately from the transaction BLOB object. This map is also added to the aggregate package after encryption with a separate key, which is not disclosed.
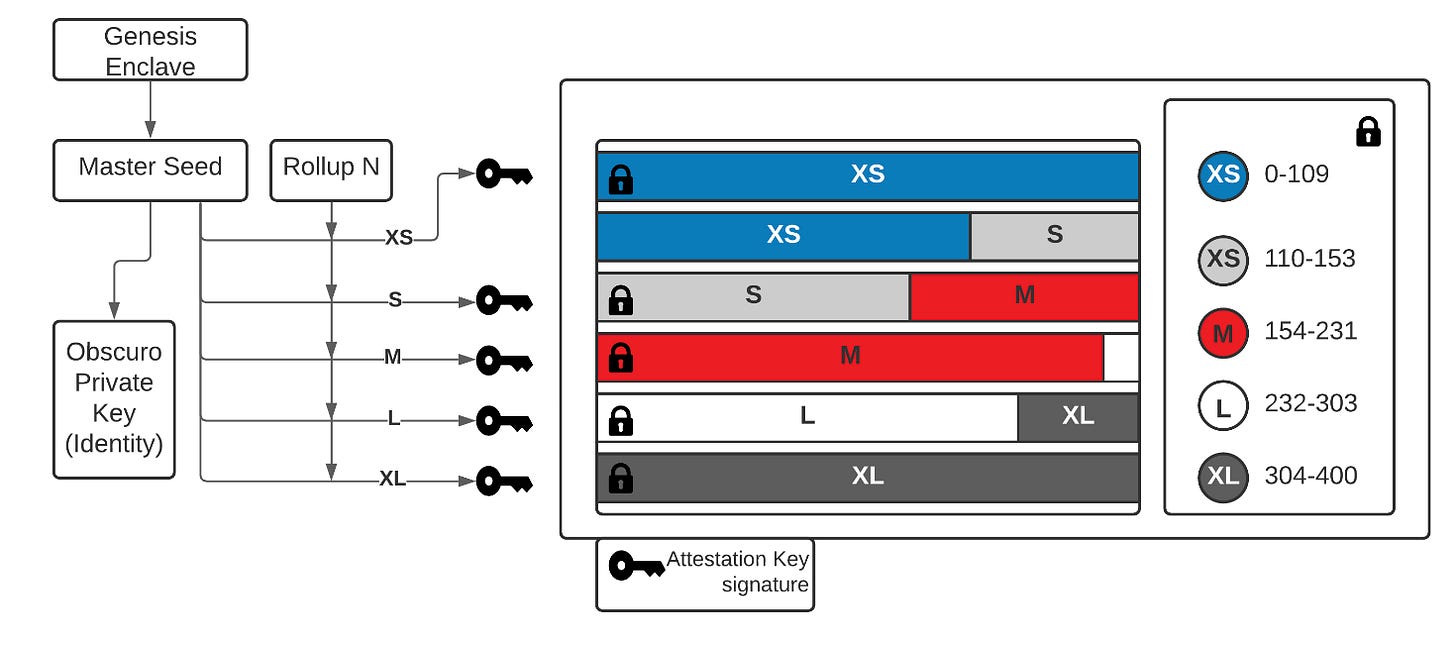
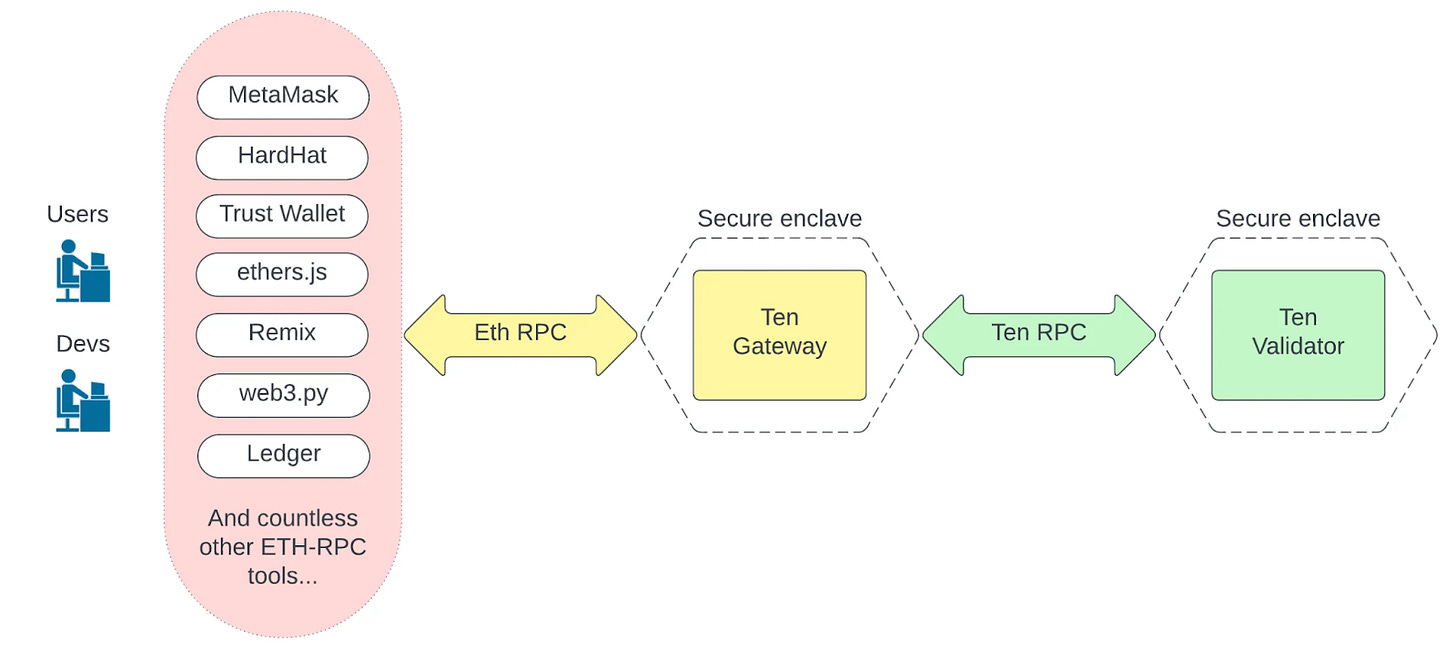
Another interesting aspect of TEN is that TEN uses a proxy mechanism to connect to wallets due to the incompatibility of the RPC API with Ethereum and L2 standard calls and structure. That is, by default, wallets do not know how to include a signed view key in every request or how to encrypt request parameters because they are working with the ETH-RPC API. So in order for users to interact through their usual familiar wallets (and the idea of proprietary wallets like Braavos greatly reduces the utilisation of the ecosystem), the team needed to come up with a way to convert requests for ETH-RPC. But also in such a way that they wouldn't have to route traffic through proxy servers, which would potentially return Mev. So the team came up with the following implementation:
TEN Gateway - running on secure enclave hardware such as nodes (with a clever mechanism to convince users that they are communicating directly with the enclave).
Local "wallet extension" - can be run on a user's local computer.
Both provide a URL that user can add to the MetaMask configuration and get all JustWork™. The first time a user uses it, they will have to sign a view key, and there is a small JS widget that simplifies this at the beginning of the user's journey.
2. TEN Network architecture
The main distinction of TEN (formerly Obscuro) from most L2 solutions (with some exceptions like Metis) is that it inherently offers a decentralized sequencer, whose nodes in TEN are referred to as aggregators. Another differentiating factor is that TEN allows for the deployment of validator nodes. Typically, in L2, this component is implemented as a smart contract on L1, and all data resides at the L1 level, enabling independent verification of proofs and construction of the current state without relying on L2 infrastructure. You can delve deeper into the principles of zk-rollups technology in our separate article, "A Deep Dive into Zk-Rollups Technology."
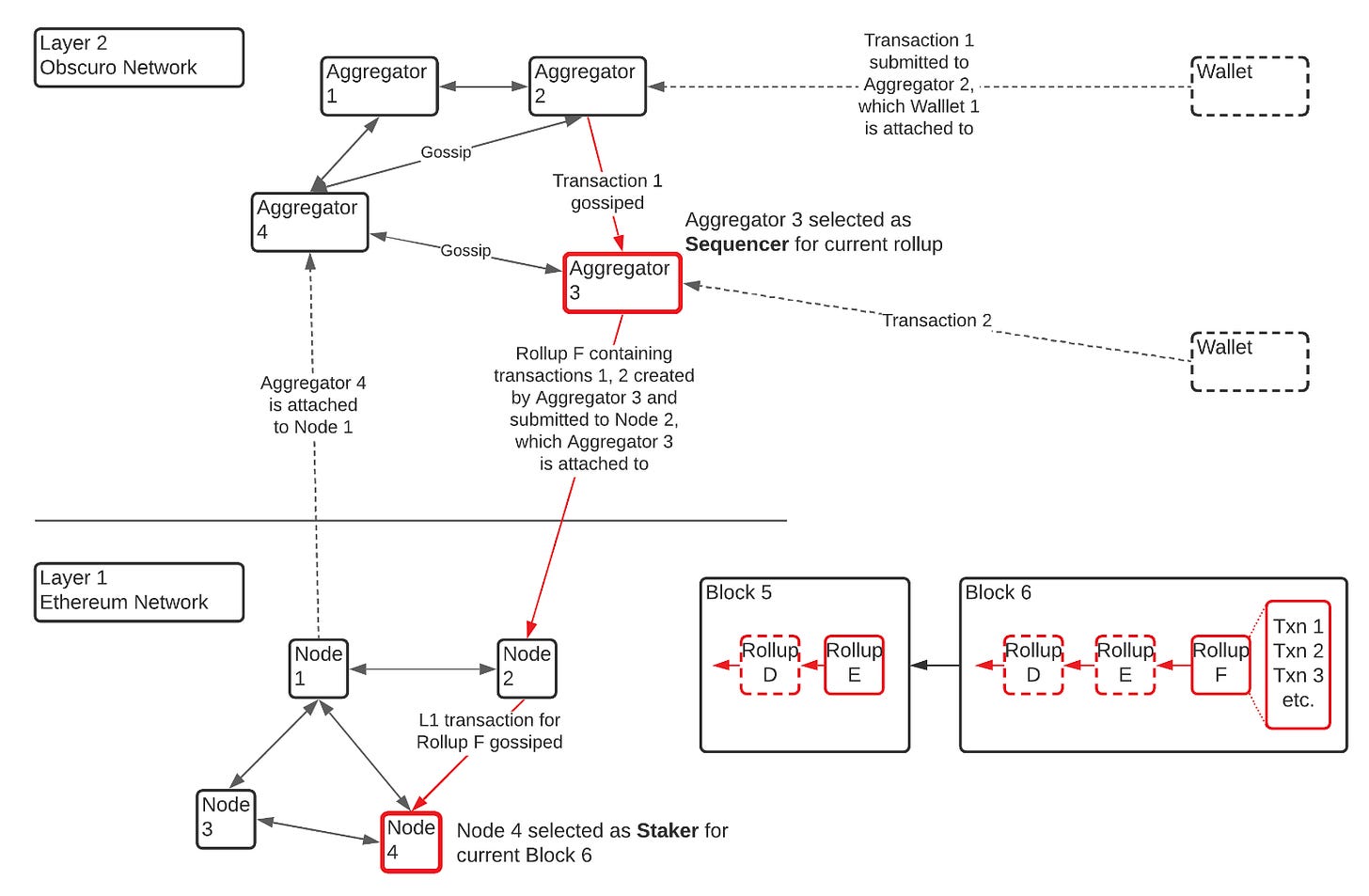
At the Layer 2 level, TEN consists of two types of nodes:
Aggregators - They compete to process user transactions, aggregate them, and send them for inclusion in Ethereum blocks. By processing messages, aggregators maintain the L2 state in encrypted TEE memory, and then register encrypted data in a local database. If they win the round, they can create a valid rollup and publish it at the L1 level. To become an aggregator, one needs to stake 50,000 tokens.
Validators - These are TEN nodes equipped with TEE, sharing a common secret, and playing a crucial role in ensuring consensus security. They are configured differently, do not stake, and are not part of the aggregator gossip network. To receive L2 transactions, they monitor the L1 network and calculate the state based on the submitted rollup data. End-users can interact with aggregators or validators to receive transaction submission events or inquire about their account balances.
Management Contract - On the L1 network, there are several standard Ethereum contracts, often referred to as Management Contracts. These contracts play a pivotal role in the functioning and management of the TEN network. This contract includes the following processes:
Network Management: This contract acts as the gatekeeper for the protocol. It manages the Secure Enclave / TEE attestation requirements, verifies attestation reports, and oversees the stake of the Aggregators.
Rollup Management: This module accepts rollups submitted by L2 nodes and collaborates with the bridge to process user withdrawal requests.
TEN Bridge: A crucial contract ensuring the security of the liquidity deposited by Ethereum end-users, mirrored in the confidential TEN ledger.
ObscuroVM - runs inside each node's TEE, deterministically chooses one of the forks as the canonical chain and only adds a convolution to it. It is essentially about the same as zkVM.
3. POBI Consensus Mechanism
The POBI (Proof of Block Inclusion) mechanism is employed as the consensus approach. In this consensus mechanism, a sequencer is randomly selected from all registered aggregators in each round. TEN's state management is similar to Ethereum's L1 blockchain. It's an account-based L2 decentralized ledger system.
TEE can generate one random one-time number in each round, and the winner of the round is the aggregator whose TEE generates the smallest random number within the group. TEEs autonomously generate these numbers and then gossip about them. Aggregators that do not win the round, akin to L1 miners, respect this decision because it is rational to act based on the incentivization mechanism. If they choose not to adhere to the protocol, they can submit a losing summary to L1, which is ignored by all compatible aggregators. This means such an aggregator would have to pay L1 gas and receive no meaningful reward. For a detailed description of the consensus mechanism, you can refer to the Obscuro whitepaper at https://whitepaper.obscu.ro/obscuro-whitepaper/consensus.html
4. Partnerships, ecosystem and direct usecases
Usually, we talk about partnerships much later in the process, but in the case of TEN, they present a unique interest as they demonstrate how an ecosystem can be built around a product. This can be considered an excellent example of how infrastructure, integrations, and partnerships should be developed around a product, unlike the standard paths of L1 and L2 development with dexes, bridges, various yield and liquidity optimizers, and so forth. TEN has a large number of applied partnerships that directly utilize this technology, better revealing the ways TEN can be used and showing that the application of TEN is indeed necessary:
Router Protocol - This integration excellently demonstrates use cases that can be connected to the Web2 world. For example, while TEN securely handles medical data, Router Protocol transfers anonymous data for research without compromising patient confidentiality. Or, Router Protocol provides transparent management of your copyright status on public chains, protecting your content while simultaneously upholding your rights, and TEN enables protection of intellectual property from unauthorized access. Or, a use case for supply chains: TEN protects confidential information, giving companies a competitive advantage. Then, Router Protocol transparently reports on product origin and compliance status, maintaining trust among stakeholders.
Paraliq Protocol - A platform for game creation, offering tools for backend, frontend, monitoring, launching referral systems, and more, allowing games to be launched in a very short time with TEN's encrypted Layer 2 providing a secure random number generator and fast, low-gas transactions, Web3 Gaming is taken to a new level.
Ridotto Io - Another bright example of using TEN for the world's first online and transparent crypto-casino.
Mummy Labs - Unlike previous games, which are online casinos, Mummy is developing an MMORPG on UE5. This is an excellent example of using TEN technology for interactive games, where it becomes possible to easily implement things like encrypted game logic, hidden maps, levels, resources, and much more with TEN's Private Shared States and Secure RNG.
NFR Islands - A great example of using TEN encryption in games, as mentioned in the protocol section. For example, a player goes on a quest and the map in front of them transforms and changes, being hidden by TEN encryption until the player completes the quest. This is a blockchain game where your actions are encrypted, your strategies are secret, and only the player determines what they will create in the end.
Cashmere Labs - Cashmere's pioneering architecture is setting a new standard for cross-chain swaps, ensuring low slippage and robust protection against MEV attacks with TEN's Encryption.
Alter Dapp - This project works on private DNS and payments, as well as other features to maintain privacy with the creation of a separate information trail. In addition to this, the ALTER package provides DAOs, NFT projects, and enterprises with secure message and data exchange. Alter is also integrated with projects such as Astro Vault, Shade, Secret, Decentr, Keplr, and others.
DEXY NTH - This is not quite an integration partnership, as above, because Dexy NTH is a trading platform and offers users trading with synthetic assets in different chains, including @tenprotocol. However, this partnership reveals TEN from a different perspective - not from the perspective of the application of the technology, but from the perspective of L2, which can have its ecosystem with its liquidity.
Context DAO - Context's private on-chain accounts allow the world to use smart contracts for automatic payments upon pre-defined conditions, and accounts receivable factoring democratizes access to liquidity for all.
Acquire Fi - With TEN's cutting-edge Layer 2 Encryption, AcquireFi plans to offer its users ultra-secure and confidential transactions, confidential digital asset transfers, private ownership, and enhanced user data protection.
Hyperlane - Thanks to Hyperlane's interchain capabilities, this partnership aims to provide a new level of intranet interaction and compatibility between blockchain networks. This collaboration not only aims to enhance user privacy and data protection but also marks a significant milestone by enabling developers to build encrypted and interoperable dApps for the very first time by combining TEN's encryption tech.
CertUP - TEN technology enables the issuance of secret NFT certificates in the form of ERC-721, containing highly sensitive personal data. TEN adds privacy by encrypting, storing, and ensuring the confidentiality of these NFT certificates, ensuring that only those who should view the data can view it.
Witnet - In addition to supporting future dApps on TEN, Witnet plans to change the way oracle data is delivered in Web3. Implementing TEN will allow for individual data provision and receipt of aggregated data confidentially.
Verida - Revolutionizing decentralized private data storage, Verida provides users with unprecedented control over their data off-chain. The partnership between TEN and Verida combines off-chain data encryption with on-chain encryption, opening up a range of new possibilities in Web3, such as exchanging private messages with shared access to multimedia, where TEN ensures chat and network resource privacy while Verida protects the privacy of shared media files.
You can view the full list of integrations and partners, which are much more, on a separate page: https://www.ten.xyz/ecosystem/. And it's worth mentioning companies such as Republic Crypto, Cryptopia, and other organizations that help TEN explore new boundaries and usage possibilities by connecting new projects.
5. Tokenomics
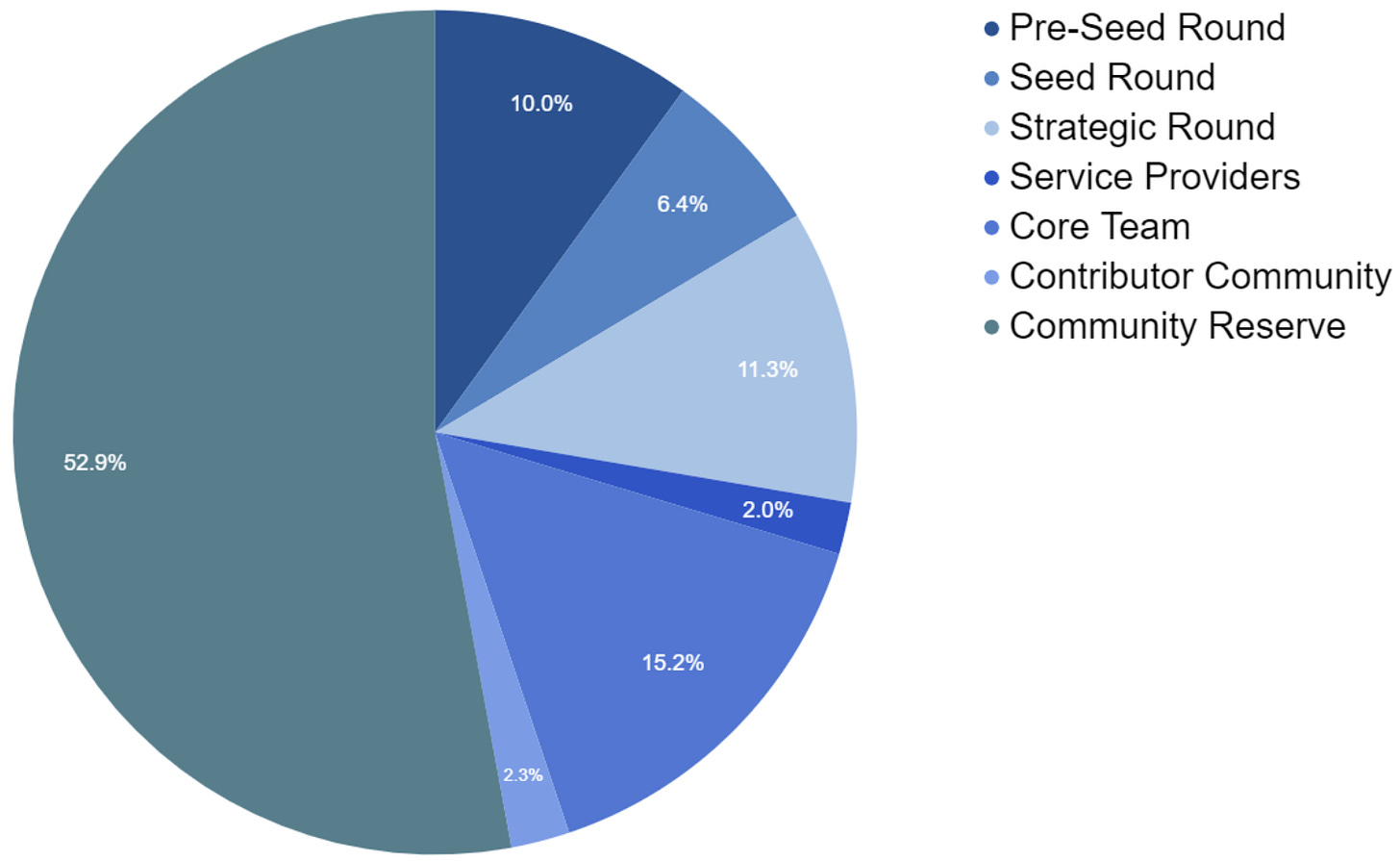
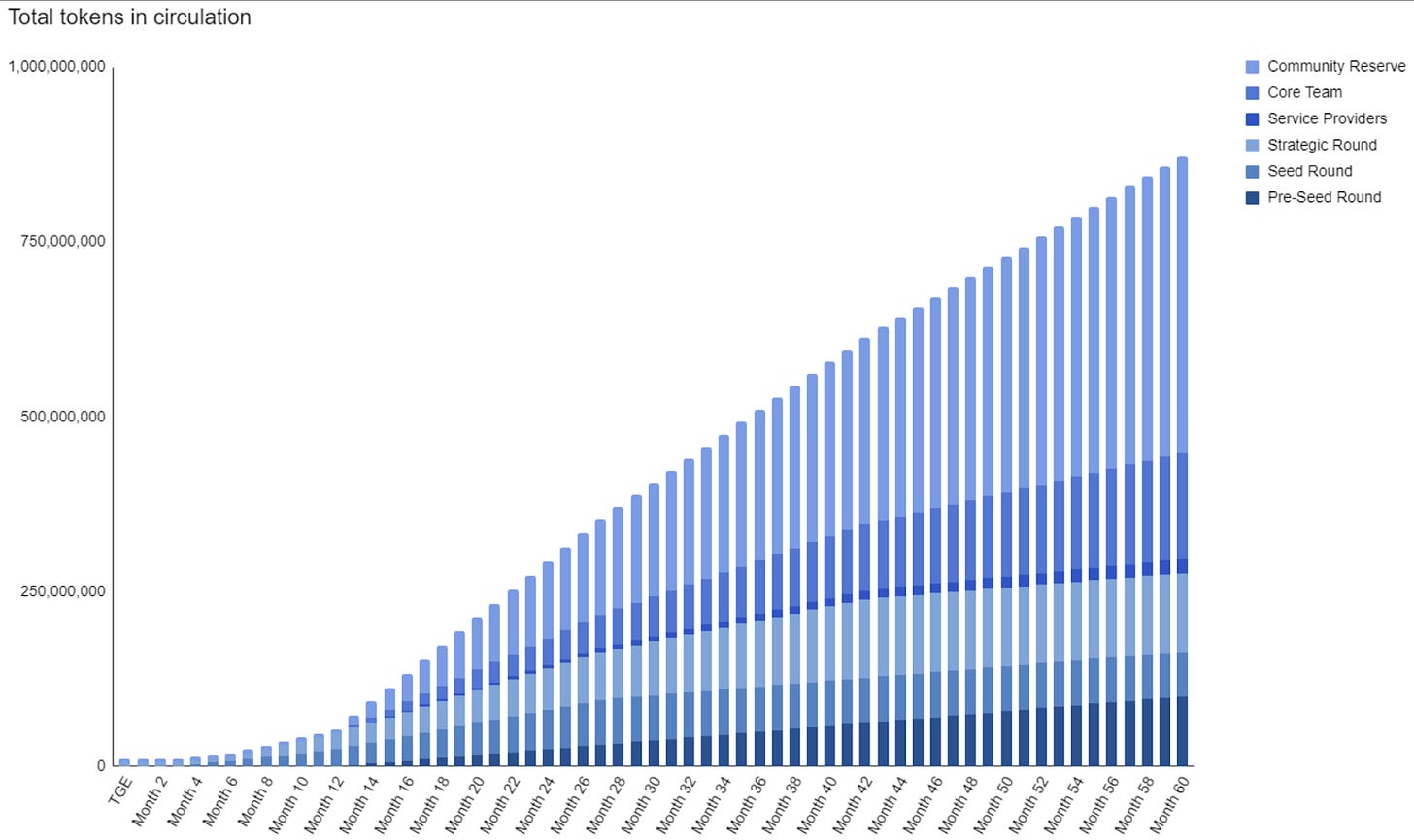
Token: TEN. The initial token supply is 1,000,000,000 TEN.
The total amount of tokens allocated to incentivized community contributions is 2.25% of the total token supply (22.5 million tokens).
At present, TEN is focusing attention on the fact that the current document represents only a preliminary version of the tokenomics, but overall it provides a general understanding of the principles of tokenomics and token usage:
Transaction fees: Initially, transactions will be paid in ETH, as in other L2 solutions, but in the future, as TEN evolves, this may be changed through governance mechanisms.
Governance: A means to vote on proposals for changes to TEN via a governance model. Governance where holding 1000 OBX tokens grants voting participation.
Staking for operators (aggregators directly involved in transaction processing): Node staking for participation in rewards. A minimum stake of 50,000 tokens (equivalent to $50k). Delegated staking available. Locked tokens can be staked.
Delegated staking, but a certain minimum stake size will be required for node operation.
Rewards for node operators, which can also cover operational expenses from these funds.
Ecosystem development incentives through grants and competitions.
Future Utility: Performance tiers on RPC via subscription paid in tokens.
Redistribution of fees captured to token holders. Redistribution of beneficial MEV back to token holders.
The initial token amount is 1,000,000,000 TEN, with no burning or minting mechanisms, but it is noted that in the future, the DAO may vote for the issuance of additional tokens.
6. Team
Previous project - the team has had time to tweak tokenisation topics: https://r3.com/products/corda/. Its features include privacy and the ability to manage data (unlike the original blockchain technology, which is based on the immutability of the records made). Transactions on Corda are not broadcast to all its participants, but only to those who have the rights to view a particular record.
The product was first introduced in 2016 and R3 set up a consortium to test its products, which included organisations such as Bank of America, BNY Mellon, Citigroup, Commerzbank, Barclays, BBVA, Commonwealth Bank of Australia, Credit Suisse, Goldman Sachs,J.P. Morgan & Co, Royal Bank of Scotland, State Street Corporation, UBS, Deutsche Bank, HSBC, Mitsubishi UFJ Financial Group, Morgan Stanley, National Australia Bank, Royal Bank of Canada, Skandinaviska Enskilda Banken, Société Générale, Toronto-Dominion Bank. Some of these clients left already in 2016-2017
James Carlyle LinkedIn Twitter - ex-founder Corda Network. As Chief Engineer of R3, James helped design Corda, and sat on R3's Executive and Risk committees. Previously, he was the Chief Engineer for Barclays Corporate Banking, co-founder of several start-ups, and holds multiple patents. James holds a degree in Mechanical and Electrical Engineering from Durham University. James has been obsessed with blockchain technology since 2014 because it appeals to his libertarian streak.
Gavin Thomas LinkedIn Twitter - ex R3 Corda engineer, As R3's Engineering COO, Gavin built and led R3's engineering function to deliver the first versions of Corda and subsequently moved to Head of PMO for all Engineering deliveries. He has previously delivered award-winning eCommerce trading platforms in tradfi markets for a global client base alongside financial regulatory programs for a world leading liquidity and data solutions provider, TP ICAP. Gavin holds a degree in Mechanical Engineering from the University of Nottingham and is a Member of the Institution of Engineering and Technology. Gavin first understood the unique value of blockchain in 2015 and has not looked back.
Tudor Malene LinkedIn Twitter GitHub - CTO, GitHub was active from 2017-2019 while working on Corda and became active again from 2022 during the start of Obscuro. Formerly a lead engineer for Corda, Tudor helped build critical components of the platform, and as a solutions architect, contributed to the success of the most important Corda projects. With 20 years of professional experience, Tudor has designed and built solutions ranging from insurance, fintech, banking to media. He holds a degree in Computer Science from the Polytechnic University of Bucharest and discovered blockchain in 2011.
Cais Manai LinkedIn Twitter - Cofounder, Head of product, ex-product in R3 Corda. Formerly Product Lead for Digital Assets, Payments and CBDC at R3, Cais has worked with some of the world's largest banks and financial institutions to develop products. Prior to R3, Cais spent 10 years in Finance, leading teams in Prime Brokerage and Equity Derivatives Trading Technology at UBS and Credit Suisse. Founder of 3 startups with 1 successful exit. Cais graduated with a degree in Computer Science from University College, London. Cais first began developing with blockchain in 2012.
Moray Grieve LinkedIn Twitter - Blockhain engineering. As R3's Head of QA, Moray helped build the test automation and processes for Corda. Before R3, Moray was a Research Physicist in Cambridge and Antarctica, spent 10 years with leading event stream processing engine Apama, and 6 years in investment banking front office. More recently, Moray built the world's largest audio database for the machine learning of sounds and delivered a groundbreaking novel geospatial database. He holds a PhD in Physics from Sheffield University and first discovered blockchain in 2017.
Stefan Iliev LinkedIn GitHub - Blockchain Developer. GitHub became active in late 2022 when Stefan started working with TEN. In the four years of designing and building blockchain solutions for the finance industry at R3, first as a blockchain engineer then R&D Engineer in the Office of CTO, Stefan has seen first hand how privacy is the key to bringing blockchain to the mainstream. Stefan's passion for cryptocurrencies dates back to the early days when Ethereum was barely above a dollar.
Pedro Gomes LinkedIn Twitter GitHub - not from R3, formerly - Ava Labs. GitHub high activity from the second half of 2018, in 2020 there was activity related to the AvalancheGo repository - so he can be considered one of the early Avalanche developers. With over 10 years of engineering experience, Pedro took a deep dive from distributed computing, performance engineering and big data to blockchain tech. As a team lead in Ava labs Pedro contributed to the Avalanche ecosystem and spearheaded the chaos and test team. Pedro holds a Masters in Computer Networking from Instituto Superior Tecnico, Lisboa.
Matt Curtis LinkedIn Twitter GitHub - not from R3, formerly - Web2. GitHub good activity since 2022, all repositories are linked to Obscuro/TEN. As a full-stack developer in the finance industry, Matt has over 10 years of experience designing and developing trading systems and trader tooling at various firms including Goldman Sachs, IG Group and Tyler Capital. He holds a degree in Mathematics from the University of Warwick and is excited to be building on blockchain technology after finally making the leap from traditional finance in 2021.
Jobin Ayathil LinkedIn Twitter - DevRel Engineer, not from R3, formerly - Arcana Network. Jobin has evangelized, advocated, and built relations with thousands of developers for 4+ years. He founded 5+ developer communities, shared his tech knowledge since his university days, and given 50+ technical talks. Passionate about empowering people to build tech, Jobin graduated in Computer Science & Engineering from Providence College of Engineering, India, and now fully immerses himself in Blockchain.
Jennifer Echenim GitHub - Senior frontend engineer. GitHub good activity since 2021 when she started working on Nestcoin and Liquality. Supremely passionate about building accessible, user-friendly, scalable web applications. Jennifer previously led the engineering team at Bloccpay and has worked with Tangerine Africa. Jennifer is committed to building communities and promoting diversity in the tech industry, and spends her free time spearheading community and technical development at Web3Afrika and Web3Ladies.
Bhaya Bakhda LinkedIn Twitter - growth manager. not from R3, formerly - Web2. He has experience as an Investment Analyst and Head of Growth in web2. Starting as a TMT analyst providing the world's top investors with primary research supplementing their fundamental analysis, Bhavya soon transitioned into growing engaged TradFi communities of $1bn-100bn AUM investors. Graduating in 2017 with an Accounting and Finance degree from Durham University, that year's crypto bull run marked Bhavya's first taste of the blockchain revolution. Today he focuses on growing Obscuro's presence by educating Web3 builders on the power of TEEs in solving inherent privacy problems.
Žiga Jokelj - engineer. Ziga, with a Master's degree in Computer Science from the University of Ljubljana, has spent over four years working in the world of blockchain. He's worked with projects like a layer 1 blockchain protocol, a mobile wallet, and Bitpanda, one of the biggest crypto exchanges in Europe. His experience and knowledge have made him a standout in the field of programming and blockchain.
7. Backers
TEN has backers such as: Dewhales Capital, Republic Capital, KuCoin Labs, R3, Big Brain Holdings, OneBlock Capital, Magnus Capital, Builder Capital, DWF Labs, Cryptopia VC, Insignius Capital, Token Metrics, Pragma Ventures, GTS Ventures, vVv, TPC Club, Cogitent Ventures and others.
Conclusion
As you may have seen, The TEN team has a long history of blockchain development. The team built the world’s most successful enterprise blockchain, Corda, which today is responsible for most of the CBDC projects being explored by central banks. TEN is a new product focused on Web3 that leverages the team's experience building Corda.TEN is the only Layer 2 with encryption and the fastest encrypted blockchain in Web3. And even as TEN has become what it is now, the team doesn't stop but continues to move forward, building the ecosystem layer by layer, forging partnerships, and integrating.
Typically, the logic behind building ecosystems and integrations for L1 and L2 involves attracting users, along with liquidity, and simultaneously, developers who create use cases and ways to utilize liquidity. In other words, this implies a centralized model, with L1/L2 at the centre, offering some advantages compared to others, or simply having good integrators and partnership relations in the team.
On the contrary, TEN offers a completely different approach. It can also form a familiar ecosystem with trading platforms, credit protocols, bridges, and so on. However, there is a significant difference: TEN allows adding specific functionality to dApps. In this case, dApps are not created for the blockchain and then add functions to it; instead, L2 TEN is used as a function for dApps. And the way this function is applied, as we have seen in practical examples in the "Ecosystem" section, is very extensive. And perhaps, the successful launch of TEN marks the transition from "Blockchains as Fat Protocols" towards "Blockchains as a Service."
TEN links:
Website | Twitter | Medium | Documentation | Discord | Telegram | GitHub